There are an estimated 13 billion IoT devices in the world and that number is expected to grow to nearly 30 billion by 2030[1]. Yet onboarding these devices onto a secure network presents a dilemma—devices need credentials to access the network, but must get on the network to obtain credentials. Furthermore, many of these devices have a limited user interface or none at all, making the process of securely onboarding them onto a Wi-Fi® network even more challenging.
The IoT onboarding procedure has traditionally been accomplished with proprietary processes that are both cumbersome and insecure— often, for example, involving a device operating as a makeshift access point (AP), security-sensitive credentials being passed in the clear, or using unique, vendor-specific procedures. In addition, given the complexities of 802.1X, most IoT devices only support WPA™-Personal network access. This means that IoT devices will share the same access credential as every other user and device, which precludes identification of individual devices on a network — a crucial security requirement for IoT networks.
There is a need for a simple, secure way to onboard IoT devices in a manner that scales from small home networks to large, complex enterprise networks that also addresses the unique requirements of IoT. Wi-Fi Alliance® has developed the Wi-Fi Easy Connect program based on the Device Provisioning Protocol (DPP) making onboarding a device as simple as scanning a QR code. In some optional deployments, onboarding with Wi-Fi Easy Connect merely entails turning the device on and walking away for a true zero-touch onboarding experience.
Wi-Fi Easy Connect – based on the DPP protocol
DPP uses modern, proven cryptographic components including elliptic curve cryptography for key establishment and the Advanced Encryption Standard (AES) for symmetric encryption. DPP is able to provision credentials for all modern WPA3™ networks, from simple passwords to X.509 certificates. DPP also defines a new credential called a Connector. This credential is much simpler to use than X.509 certificates (they do not have the ASN.1 baggage that certificates do) but, unlike pre-shared keys (PSKs) and passwords, Connectors are bound to a physical device thereby allowing for IoT devices to be uniquely identified on the network and have device-specific access controls and authorization policies applied to it.
The DPP protocol is performed by two entities, the Enrollee device wishing to be onboarded, and the Configurator, which is responsible for authenticating the Enrollee and provisioning it for the network. With DPP, the Configurator could be a smartphone or other mobile device, or it could be a device fixed in the network such as an access point (AP), switch, or router. The only requirement is that both the Enrollee and the Configurator have access to an interface that enables Wi-Fi connections. The DPP protocol is also supported over TCP/IP connections, allowing for a centralized controller to act as a Configurator and use a multitude of APs for its Wi-Fi communication.
Prior to the start of the DPP protocol, a Configurator is provided with a uniform resource identifier (URI) which contains the Enrollee’s bootstrapping public key by scanning a QR code, touching an NFC tag, or downloading the information from a device manufacturer’s cloud. When powered on, Enrollees then begin to chirp, or securely broadcast a notification of the presence of an unprovisioned thing to nearby Configurators. If a Configurator possesses the device’s bootstrapping key, it can then initiate the DPP protocol to authenticate and provision the device. Only a valid Configurator with the Enrollee’s bootstrapping key can initiate the DPP protocol, thereby preventing attackers from hijacking an unprovisioned device.
Bootstrapping with Wi-Fi Easy Connect
Bootstrapping is the act of gaining trust in an Enrollee’s public key. Every Wi-Fi Easy Connect Enrollee has a public/private key pair that is used by the DPP protocol to authenticate the device. Once a public key is trusted, it can be used to discover, uniquely identify, and authenticate the IoT device.
There are four options for bootstrapping with Wi-Fi Easy Connect:
- Scanning a QR code: The IoT device’s public key is encoded into URI form and then into the QR code, which may be affixed to the device or any packing list associated with the device. Scanning the QR code extracts the URI containing the device’s public key which is then stored in a Configurator’s DPP URI database;
- Cloud-based: A Configurator can interact with an IoT device manufacturer’s cloud service to obtain the DPP URIs of devices the customer has purchased. This can be a push model in which bootstrapping is part of processing of the purchase order and the manufacturer pushes DPP URIs to a customer cloud tenancy, or it can be a pull model where purchased devices are identified—e.g. with a serial number—to the manufacturer and the DPP URI is obtained by the Configurator;
- Near Field Communication (NFC): Proximity of a Configurator and Enrollee can be used to exchange DPP URIs using NFC using a tap-and-go interaction;
- PKEX: A secure password-authenticated key exchange in which the Configurator and Enrollee parlay a simple password into mutually-trusted public keys through their respective user interfaces.
Flexible deployment of Wi-Fi Easy Connect
Wi-Fi Easy Connect can scale from a variety of network sizes, including home, office, and enterprise networks, as long as the appropriate Configurator is deployed.
Home network
Employing a Configurator in an AP/router is a convenient way of supporting Wi-Fi Easy Connect in a home network. The Configurator will use the vendor-supplied UI to be provisioned with information about the credentials and SSID used in the home network. If the AP/router is managed by a service provider, it can be provisioned to support the customer’s home network by the ISP (figure 1).
An app running on a mobile phone or tablet can scan an Enrollee’s QR codes and communicate the URI information to the Configurator on the AP/router using a secure, DPP-defined REST API. When the IoT device is turned on, its chirps will be received by the AP and the device will be automatically on-boarded.
Small and remote office
Small office deployments of Wi-Fi Easy Connect resemble home office deployments. The Configurator can reside in an AP/router and utilize an app running on a mobile device to populate the DPP URI database on the Configurator using a DPP-defined REST API.
Remote offices can take advantage of local APs to communicate using Wi-Fi Easy Connect on behalf of a centralized Configurator in the main office. In these deployments, IPsec-protected DPP-over-TCP can be used to bridge the conversation between the local Enrollee and the central office Configurator. In addition to the app running on a mobile device, remote office deployments can take advantage of cloud-based bootstrapping. Unprovisioned devices whose DPP URI is already populated in the Configurator database can be drop-shipped to the remote office, at which point the IoT device simply needs to be powered on for it to be automatically discovered, authenticated, and provisioned for the local network of the remote office. Or, the app can be used to add locally obtained devices to the Configurator’s URI database for rapid onboarding.
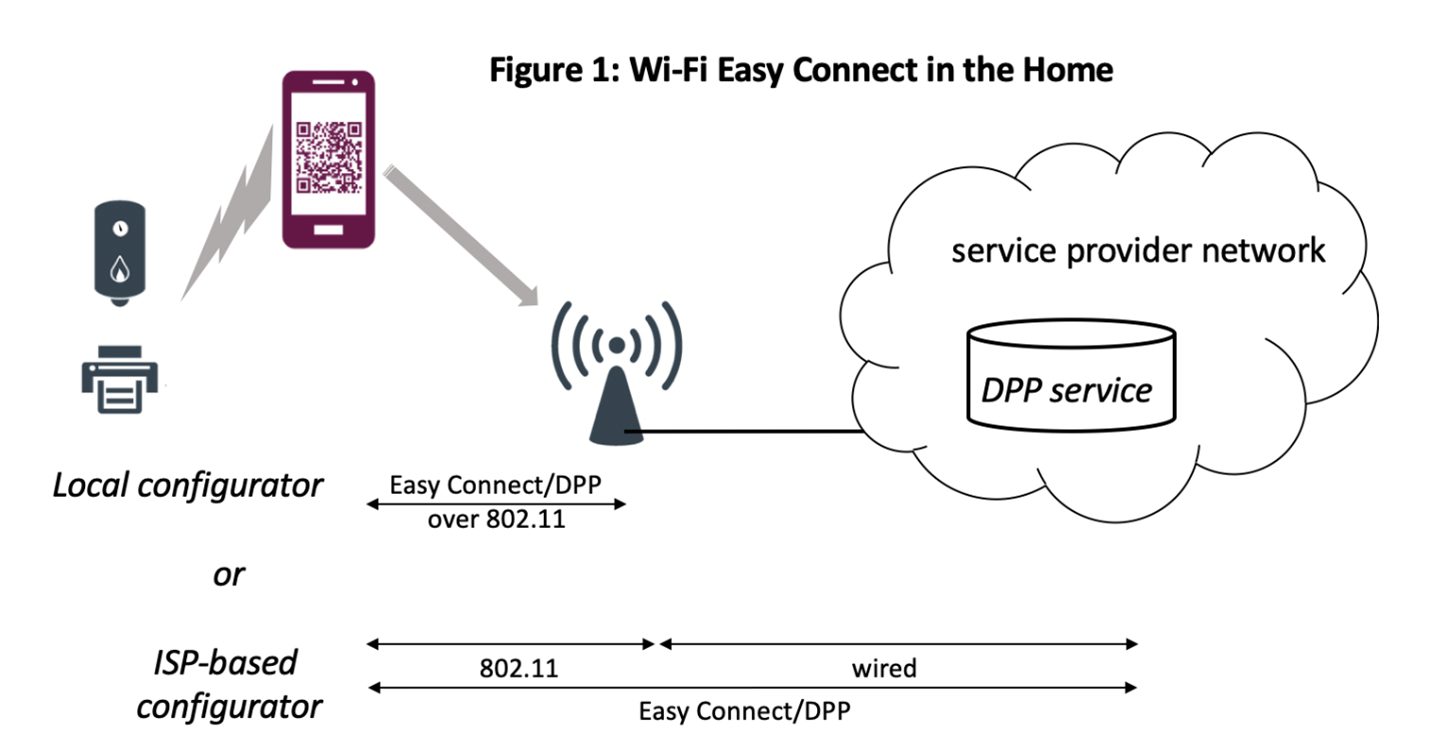
Large enterprise
Large enterprise Wi-Fi networks are typically handled with a multitude of APs that communicate with centralized controllers. This type of deployment is well-suited to DPP when the centralized controller is the Configurator, or when a network Configurator service exists to which various controllers communicate. APs connect to these controllers and bridge the DPP conversation back using DPP-over-TCP (figure 2).
Cloud bootstrapping can be used to populate a Configurator’s DPP URI database to perform bulk onboarding of hundreds of IoT devices. In addition, a vendor’s app running on a mobile device can scan QR codes for IoT devices whose manufacturer does not support cloud bootstrapping. This can result in true zero-touch onboarding at scale – devices can be provisioned for network access as quickly and easily as turning them on.
Challenging deployments
Some Wi-Fi deployments occur in challenging environments, like an offshore oil rig or the core of a nuclear reactor, where sensors, monitors, and controllers are needed to conduct a safe operation. Traditionally, provisioning of these devices was a challenge because the personnel with IT expertise typically did not have access to the location the device needed to be installed, and those with access typically had expertise in other fields. Wi-Fi Easy Connect allows personnel with no IT or networking expertise to install a device in a challenging area simply by turning it on.
Key takeaways
Wi-Fi Easy Connect creates an easy, effective onboarding experience for a variety of use cases, thanks to the flexibility of DPP. When deploying or upgrading a network, consider building in Wi-Fi Easy Connect support to the network you’re deploying – from small home networks to large enterprise networks – and discuss Wi-Fi Easy Connect support with IoT vendors for a simple, secure onboarding experience, even in complex IoT environments.
[1] https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/
The statements and opinions by each Wi-Fi Alliance member and those providing comments are theirs alone, and do not reflect the opinions or views of Wi-Fi Alliance or any other member. Wi-Fi Alliance is not responsible for the accuracy of any of the information provided by any member in posting to or commenting on this blog. Concerns should be directed to info@wi-fi.org.
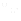



Add new comment