As mentioned in the previous post in this series, the Wi-Fi Alliance® update to Wi-Fi CERTIFIED WPA3™ includes features that provide Wi-Fi® devices with additional safeguards against a variety of attacks, including man in the middle (MITM) and evil twin attacks.
The previous post focused on Operating Channel Validation (OCV) and Beacon Protection. In this post, we will explore the details of two additional new features: SAE Public Key (SAE-PK) and Transition Disable. SAE-PK provides protection against evil twin attacks on client devices in public networks that use WPA3-Personal, while Transition Disable provides protection against active downgrade attacks on client devices operating in a transition mode with WPA3-Personal, WPA3-Enterprise or Wi-Fi Enhanced Open™.
SAE Public Key
Although WPA3-Personal is intended for private networks, it is also commonly used in small public networks, such as cafes, restaurants, and meeting venues. In such cases, the network administrator typically shares a single password with multiple users. While access to the network can be controlled by judicious sharing of the password—often via signage only visible to customers—it may be relatively easy for an attacker to find out the password, which is sufficient to launch an evil twin attack.
Figure 1: SAE-PK credential generation
Such attacks are prevented by an extension to WPA3-Personal called SAE-PK. As shown in the example in Figure 1, the network administrator generates SAE-PK credentials and configures them on APs in the network, then distributes the password to users. The AP credentials comprise an Elliptic-Curve public key pair, a random Modifier value, and a specially generated password which encodes a fingerprint of the public key concatenated with the Modifier.
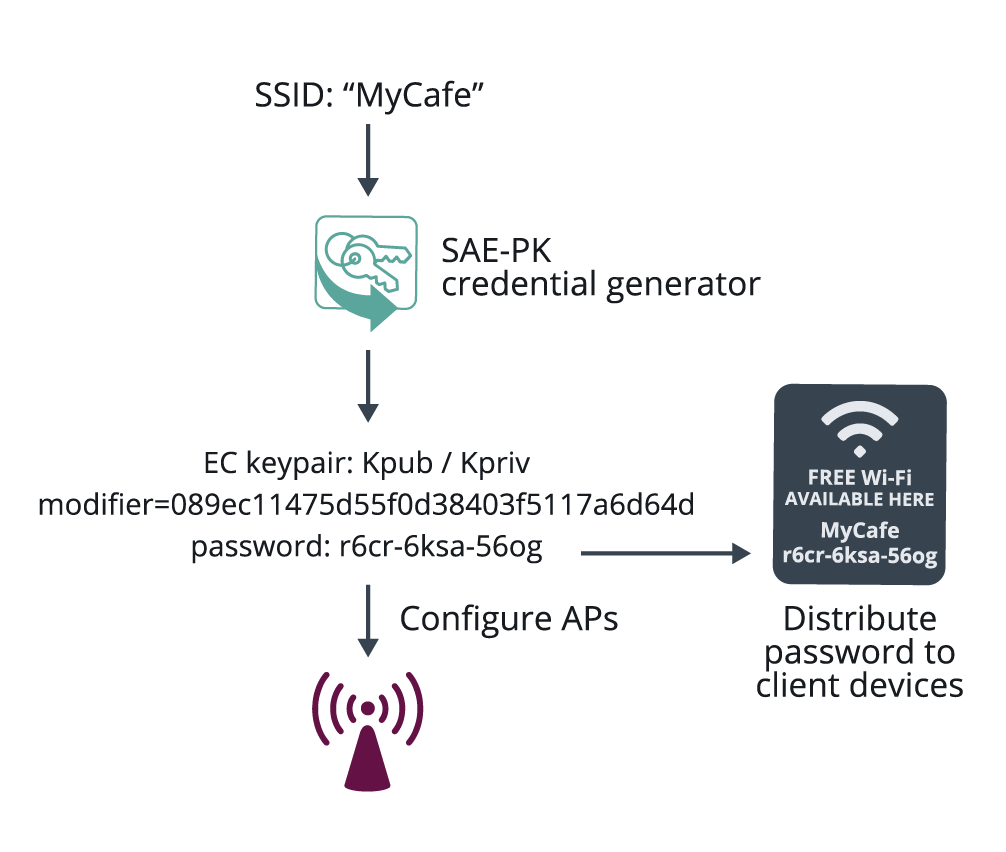
Figure 2: SAE-PK authentication
The SAE-PK authentication exchange is very similar to the regular SAE exchange, with the addition of a digital signature sent by the AP to the client device, as shown in Figure 2. The client device validates the public key asserted by the AP based on the password fingerprint, and verifies the signature using the public key. Even if the attacker knows the password, it does not know the private key to generate a valid signature, and therefore the client device is protected against an evil twin attack. The SAE-PK design makes it computationally infeasible for the attacker to find its own key pair and Modifier that matches the fingerprint in the password.
When SAE-PK is enabled on a WPA3-Personal network, the same password is shared with all users, including those with legacy devices. Client devices that support SAE-PK are protected against evil twin attacks without any change to the end user experience.
Transition Disable
WPA3 defines transition modes for client devices so that they can connect to a network even when some of the APs in that network do not support the strongest security mode. Client device implementations typically configure network profiles in a transition mode by default. However, such a client device could be subject to an active downgrade attack in which the attacker causes the client device to use a lower security mode in order to exploit a vulnerability with that mode.
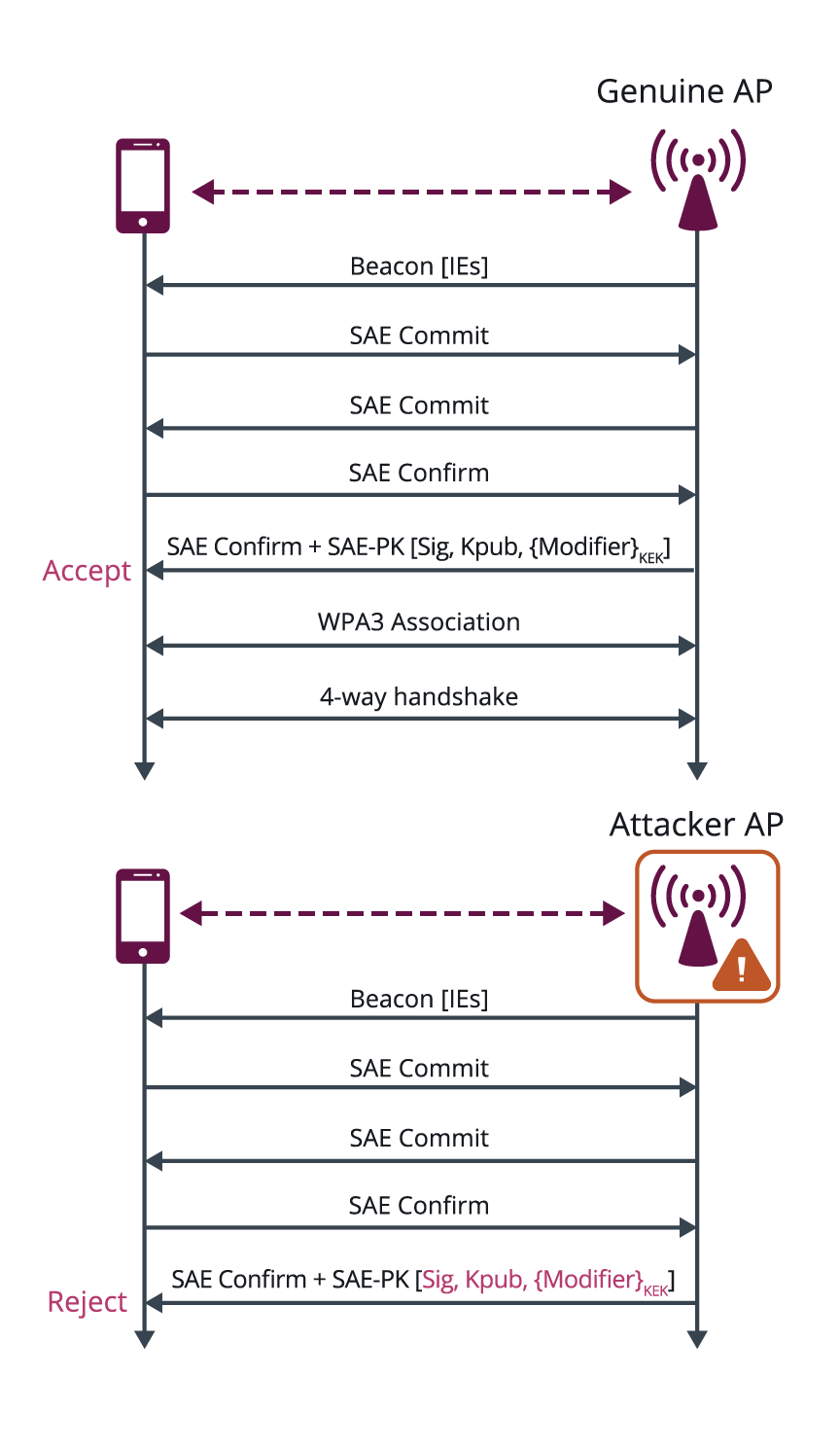
Figure 3: Transition Disable
WPA3 has introduced the Transition Disable feature to mitigate such attacks, by enabling client devices to change from a transition mode to an “only” mode when connecting to a network, once that network indicates it fully supports the higher security mode. For example, as shown in Figure 3, if all APs in a network support WPA3-Personal, the AP indicates this to the client device in the protected Transition Disable key data encapsulation (KDE), which then configures the profile for that network to be WPA3-Personal Only. Hence, the client device is protected from active attacks that leverage its support for legacy WPA2-Personal protocol. The new configuration is stored by the client device in its network profile, so it is protected whenever subsequently attempting to connect to that network.
New WPA3 features provide advanced security for Wi-Fi devices
SAE-PK and Transition Disable, as well as the two features described in the first post of this series provide substantial new capabilities to protect Wi-Fi devices against various kinds of active attacks. More information on these features is available in the Wi-Fi CERTIFIED WPA3™ Technology Overview. The December 2020 WPA3 update offers the most sophisticated Wi-Fi security available, helping ensure that users both at home and in the office can connect to work, learn, and socialize with greater peace of mind.
The statements and opinions by each Wi-Fi Alliance member and those providing comments are theirs alone, and do not reflect the opinions or views of Wi-Fi Alliance or any other member. Wi-Fi Alliance is not responsible for the accuracy of any of the information provided by any member in posting to or commenting on this blog. Concerns should be directed to info@wi-fi.org.
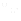



Add new comment