This is the first installment of a two-part series exploring recent WPA3™ enhancements.
The ubiquity of Wi-Fi® deployments and rapid growth in the volume and diversity of Wi-Fi devices represents an attractive attack surface for hackers to exploit. However, thanks to the strong cryptography and protocols provided by Wi-Fi CERTIFIED WPA3™, together with robust implementations, Wi-Fi devices are more secure than ever.
Figure 1: Multi-channel man in the middle attack
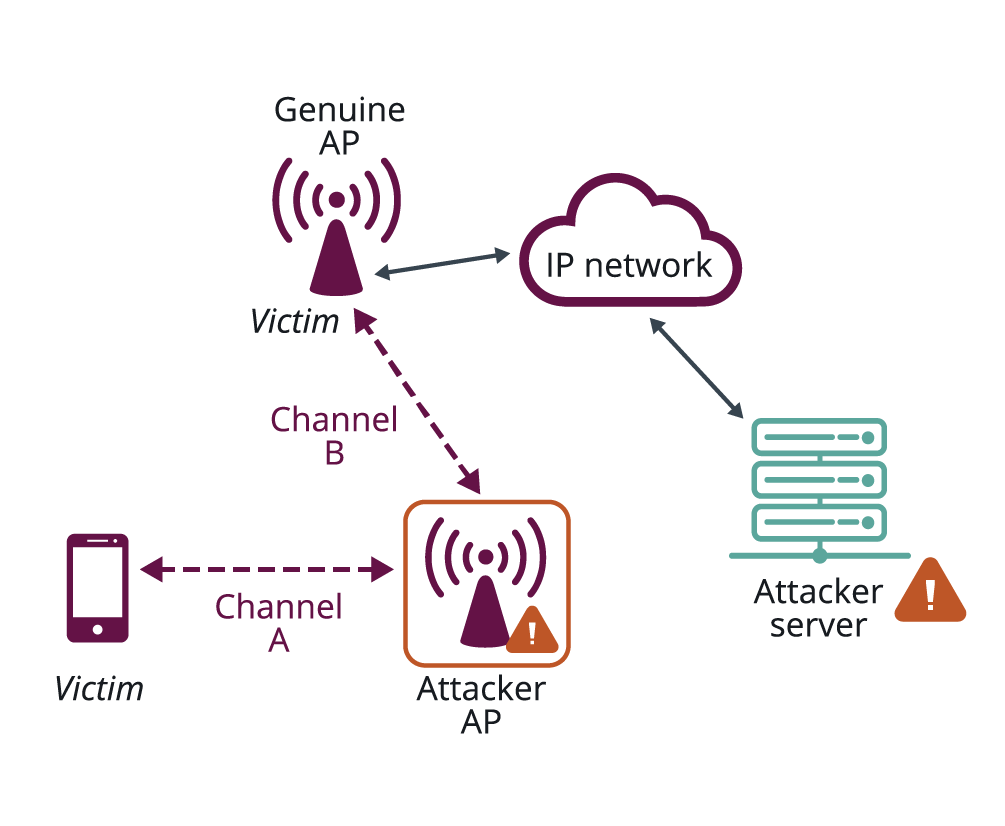
The launch of WPA3-Personal in 2018 introduced protection against dictionary attacks when password authentication is used. Subsequent updates to WPA3 in December 2019 and December 2020 have introduced additional defenses against active attacks. For instance, WPA3 helps prevent man in the middle (MITM) attacks, such as the multi-channel attack shown in Figure 1, that try to exploit a protocol or implementation weakness by relaying, suppressing, modifying, or injecting messages. Additionally, WPA3 helps prevent evil twin attacks where, as shown in Figure 2, an attacker masquerades as a legitimate access point (AP) to inspect or modify data, or attempt social engineering attacks to obtain personal information.
Figure 2: Evil twin hotspot
The defenses against active attacks introduced in the WPA3 December 2019 update were focused on WPA3-Enterprise, introducing server certificate validation requirements to protect against evil twin attacks when EAP-TLS, EAP-TTLS or EAP-PEAP are used.
In this two-part series, we outline the benefits and operation of additional features introduced in the more recent WPA3 December 2020 update, which offer protection against other kinds of active attacks. In this first part, we will explore the details of two new features which apply to both WPA3-Personal and WPA3-Enterprise: Operating Channel Validation (OCV) and Beacon Protection.
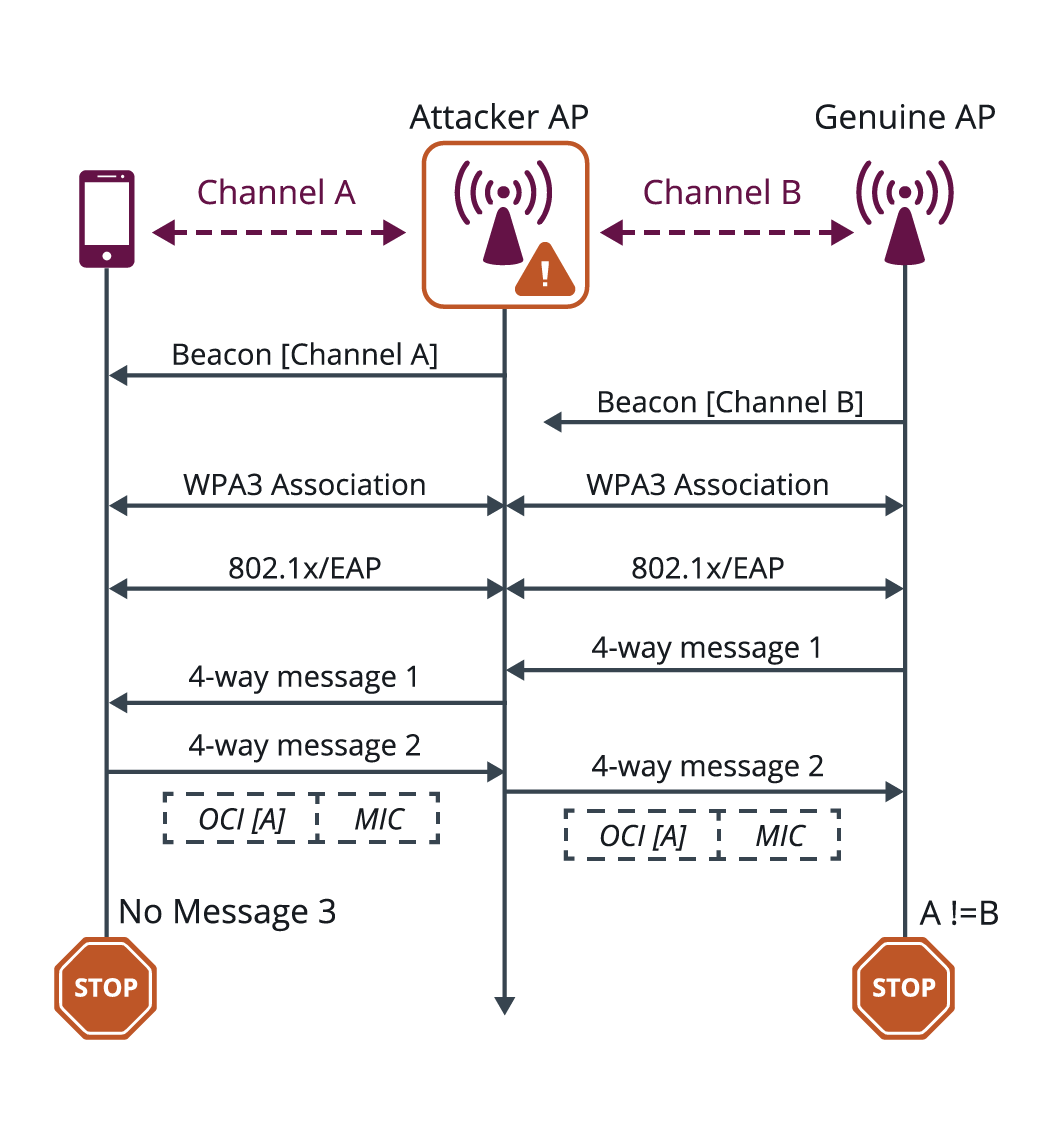
Operating Channel Validation (OCV)
It has been well known for some time that active attacks can exploit the lack of authentication of service attributes used for discovery and subsequent security negotiations. Such vulnerabilities have been exploited in various technologies. In the case of Wi-Fi, one such service attribute is the Operating Channel Information (OCI)—or the frequencies, bandwidth, and power limits—used for communication between an AP and its Wi-Fi clients. Lack of OCI authentication was exploited in KRACK attacks to enable the attacker to obtain a multi-channel MITM position. WPA3 has introduced OCV, which authenticates OCI to protect against any other potential exploits that might use a channel-based MITM attack.
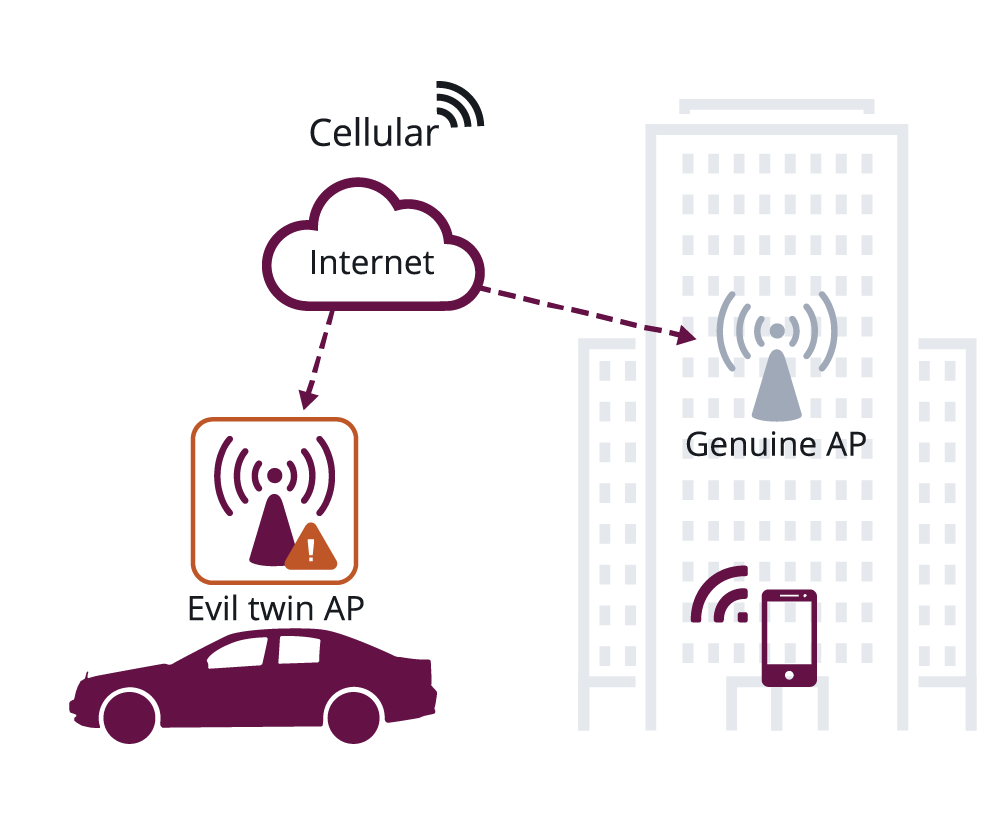
Figure 3: Operating Channel Validation
Figure 3 illustrates OCV operation in a WPA3 association that uses 802.1X/EAP for authentication, followed by the standard 4-way handshake to confirm the keys. The OCV feature adds OCI to the handshake. If the AP detects that the information does not match the channel on which it is received, the confirmation is aborted. OCV also enables the same confirmation to be performed by the station (STA). Therefore, an attacker will not be able to obtain a channel-based MITM position, and this class of active attacks is avoided. OCI is also confirmed in other security-related Wi-Fi exchanges, such as Fast Basic Service Set Transition (FT) and Fast Initial Link Setup (FILS) authentication, and also whenever a channel switch occurs.
Beacon Protection
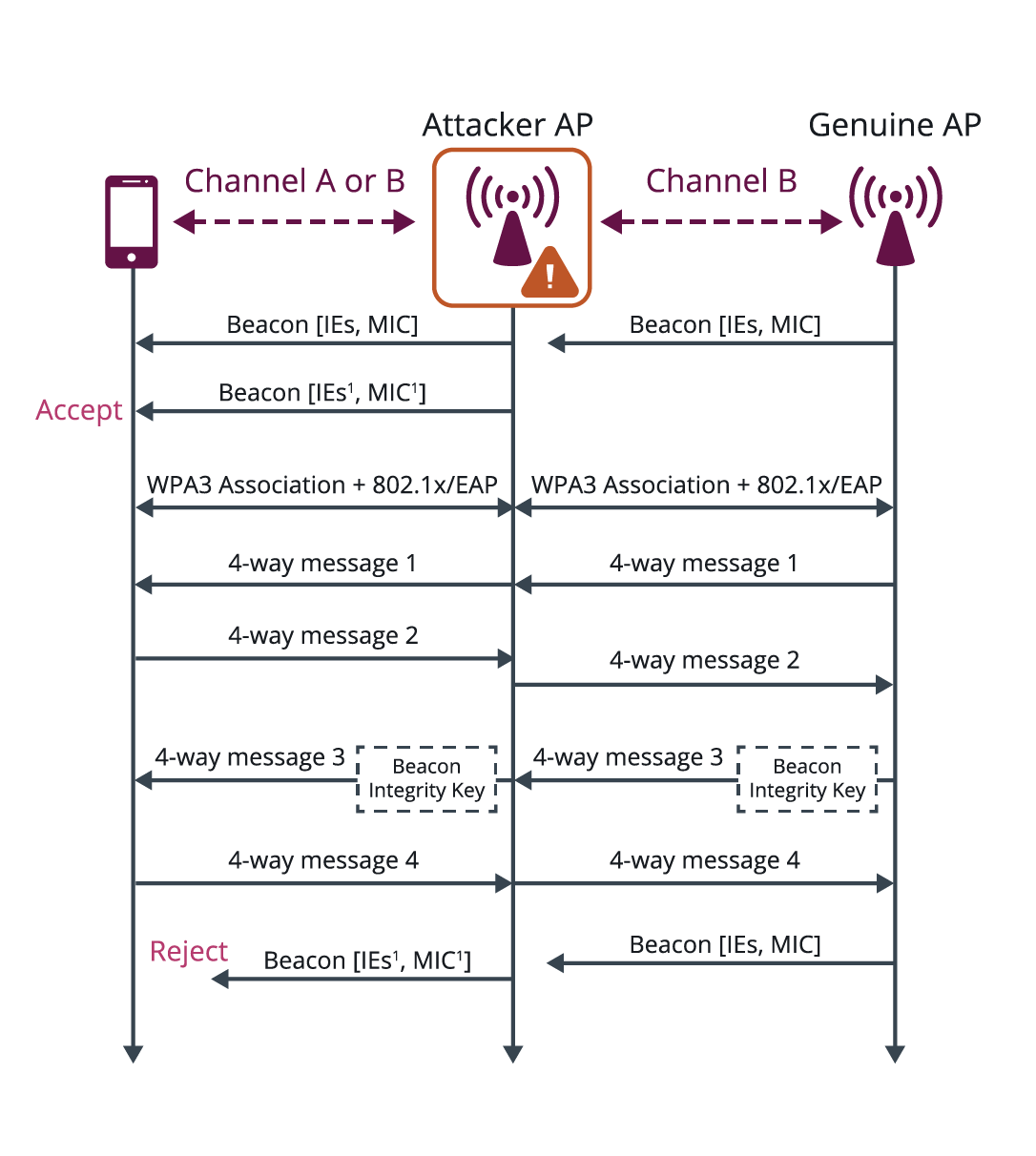
Another class of active attacks attempts to exploit any unauthenticated signaling of capability and operating parameters between devices. In the past, the Wi-Fi capabilities and additional signaling advertised in Information Elements (IEs) within Beacon frames were unprotected. WPA3 has introduced Beacon Protection, whereby an AP provisions its clients with the AP’s Beacon Integrity Key during security association setup and adds a message integrity check (MIC) element to Beacon frames that covers all but the timestamp field of the Beacon frame contents. This allows clients that are associated with the AP to verify the Beacon frame integrity, and detect active attacks that forge or modify Beacon frames. This prevents active attacks in which the Beacon frame IEs are altered to cause client devices to, for example, consume more power, use lower data rates, or incorrectly switch channels.
Figure 4: Beacon protection
WPA3 provides additional protection against active attacks
The WPA3 December 2020 update provides substantial new capabilities to protect against various kinds of active attacks, such as man in the middle attacks and evil twin attacks. More information on these features is available in the Wi-Fi CERTIFIED WPA3™ Technology Overview. WPA3 offers the most advanced Wi-Fi security available, ensuring both home and enterprise users can connect to work, learn, and socialize with peace of mind.
The statements and opinions by each Wi-Fi Alliance member and those providing comments are theirs alone, and do not reflect the opinions or views of Wi-Fi Alliance or any other member. Wi-Fi Alliance is not responsible for the accuracy of any of the information provided by any member in posting to or commenting on this blog. Concerns should be directed to info@wi-fi.org.
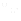



Add new comment